Scams
Case Studies
Learning & Information
Don't Get Rekt By PDFs
Apr 19, 2024 | 6 min read
Malicious PDFs are increasingly used by threat actors to deliver malware as Microsoft tightens security on Office files. Outdated PDF readers and social engineering tactics pose major risks - especially to Web3 users - keeping software updated, disabling scripting, and verifying sources before opening any PDF is vital.

PDFs are a popular file format that have been in use since 1993. However, the love for PDFs is not just shared by legitimate users, but also threat actors who often weaponize the file format in order to deliver malware. Malicious PDFs can be dated back to 2001, when the “ Peachy ” malware was first identified. While the Peachy worm was rather benign by modern standards, malware development and the weaponization of PDFs has (unfortunately) come a long way, and the use of PDFs by threat actors is on the rise.
Why Are Malicious PDFs Becoming More Popular?
The rise of malicious PDFs over the past few years is directly related to efforts by Microsoft to curtail the use of MS Office documents (.docx, .xlsx, etc) to deliver malware. Since the introduction of security changes by Microsoft which have blocked macros by default, threat actors have had to resort to other tactics, techniques and procedures (TTPs) to deliver their malware and drive the success of their criminal activities. It is important to note that trends in the use of malicious PDFs are also linked to new vulnerabilities found within the software used to read the file type such as Adobe Reader.
Furthermore, the creation of malicious PDFs is simple. Builders/wizards are available on common repositories like GitHub and also for sale on criminal marketplaces. This ease of access makes PDFs accessible for even novice threat actors.
The Different Types of Malicious PDFs
Links & Redirects
Thanks to advances in patch management and user awareness, the majority of malicious PDFs now rely upon social engineering rather than code execution for their exploits. Below is a mock example of a PDF seeking to socially engineer user interaction.
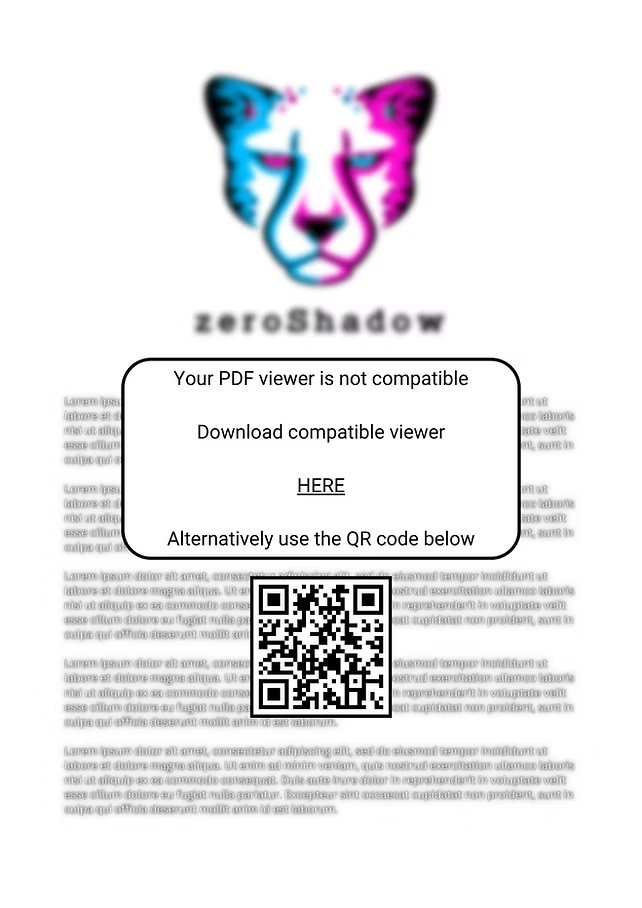
This example uses the following common TTPs:
- Hiding what appears to be the legitimate file behind a blurred filter or other obfuscation.
- An overlaid message directing the user to take some action in order to see the document correctly.
- A hyperlink or clickable item which will likely direct the user to either a phishing page designed to capture credentials, or a website hosting malware which will then be downloaded to the victims machine.
- Some campaigns also include a QR code, designed to be scanned by a mobile device, which will either direct the user to either a phishing page designed to capture credentials, or a website hosting mobile malware (.apk).
This example is relatively simple, but threat actors often go to great lengths to create convincing lures, often using social engineering tactics such as pretexting , a need for urgency or the illusion of a reward. Threat actors also use themes that are targeted to the specific victim, such as a job offer or accusation, or are linked to current affairs/geopolitics. For instance, the coronavirus pandemic led to a surge of malicious documents and phishing using pandemic related clickbait titles to drive interaction.
Code Execution
The PDF file format contains scripting technologies which are designed to add useful and interactive features to PDFs. Unfortunately this also allows threat actors to include malicious code seeking to exploit vulnerabilities in the PDF reader software in order to impact the wider machine in some way. If you’re using a vulnerable PDF reader, simply opening a malicious PDF can compromise your machine.
For instance outdated versions of Adobe Reader or Foxit Reader can be exploited thanks to a myriad of different vulnerabilities. An example of this would be CVE-2023-27363 , a vulnerability in Foxit Reader, which was reportedly used to target members of the crypto community with lures relating to discussions about a new project. The malicious PDF ultimately would have led to infection with the commodity infostealer StealC , which would have stolen credentials, cookies and files from the victim machine. This stolen data could then be used to further compromise the victim or their organization.
Unfortunately this is not just isolated to standalone viewers like Adobe Reader or FoxIt Reader, but also PDF readers included in browsers such as Google Chrome. A search on Mitre.org reveals 108 separate vulnerabilities in PDFium, the engine used by Google Chrome to read the PDF file format. While these vulnerabilities vary in terms of exploitability, impact and risk, it demonstrates the risk of a threat actor developing or purchasing a 0-day exploit in a PDF reader as being real and worth considering.
zeroShadow have investigated incidents involving the deployment of malware that total almost $48M USD in cryptocurrency thefts. It is clear that malware is a big part of threat actors TTPs, and malicious PDFs are certainly part of that arsenal.
The Risk To Web3
Organizations and individuals working in web3 are at a higher level of risk when it comes to attack by threat actors. This is for several reasons:
- Money is involved, and this incentivizes criminals who will seek to steal it.
- Many people incorrectly store private keys in ways that can be easily stolen through the deployment of infostealers or backdoor malware.
- The nature of crypto lends itself to social engineering, pretexting and urgency, no one wants to miss out on opportunities and threat actors leverage this.
- Anonymity is often a driving factor in many people's interest in crypto, threat actors know this and abuse this factor…do you really know who you’re talking to?
Since August 2023, zeroShadow have investigated incidents involving the deployment of malware that total almost $48M USD in cryptocurrency thefts. It is clear that malware is a big part of threat actors TTPs, and malicious PDFs are certainly part of that arsenal.
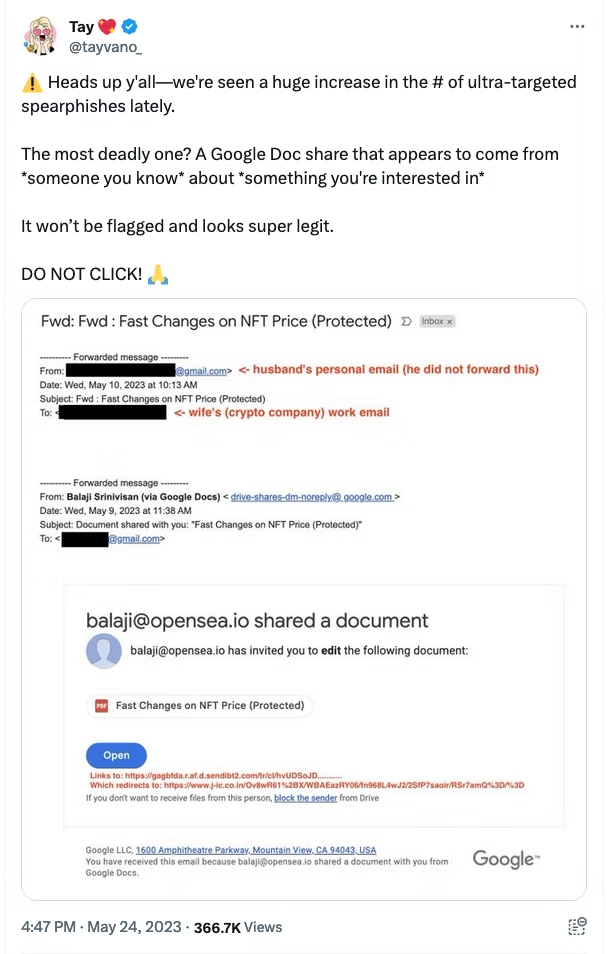
What Can I Do To Mitigate The Risks?
Just because threat actors are increasingly using malicious PDFs in their attacks, doesn’t mean we should all just abandon and ignore every PDF we receive. But there are a few things we can do to help mitigate the risk of malicious PDFs:
- Always keep your PDF reader updated, whether that be a standalone application or your internet browser. Remember, this might not be an automatic process and you must include it in your patch management plans.
- Wherever possible, change settings so that scripting and external sources are disabled in your PDF reader.
- Never store credentials or private keys within your browser or in plaintext, they are vulnerable to infostealer malware! Always use a password manager which you have thoroughly researched and trust.
- Make use of security solutions such as antivirus (AV) and endpoint detection (EDR).
- Question…Do you know who sent you this file? Have you confirmed via a known and trusted contact that this communication is legitimate?
- Consider…Were you expecting this communication? Or is it unsolicited and unconnected to a previous matter.
- Examine…How was this file delivered? Does it match normal processes, or is something different? Does the filename seem like clickbait or unusual.
- If you need to receive PDFs from untrusted sources, such as when advertising a job role, consider setting up a standalone email address or other correspondence.
- When dealing with untrusted or suspicious files, it is best practice to open them in an isolated environment, such as a sandbox or virtual machine. That way if malware is detonated, the environment can be destroyed/reset with limited impact.
Public malware analysis platforms like VirusTotal , Joe Sandbox , AnyRun or many others can be useful in identifying malicious behavior. WARNING: samples uploaded to these services are public, do not upload sensitive or confidential content.
Original article by the zeroShadow team
